Towards the end of 2008, we brought online a new datacenter to serve the over 5.5 million blogs now hosted on the WordPress.com platform. Adding the data center in Chicago, IL gives us a total of 3 data centers across the US which serve live content at any given time. We have decommissioned one of our facilities in the Dallas, TX area. Our friends at Layered Technologies were kind enough to shoot this footage for us (think The Blair Witch Project) and the always awesome Michael Pick took care of the editing. Here’s a peak at what a typical WordPress data center installation looks like…
For those interested in technical details here is a hardware overview of the installation:
150 HP DL165s dual quad-core AMD 2354 processors 2GB-4GB RAM
50 HP DL365s dual dual-core AMD 2218 processors 4GB-16GB RAM
5 HP DL185s dual quad-core AMD 2354 processors 4GB RAM
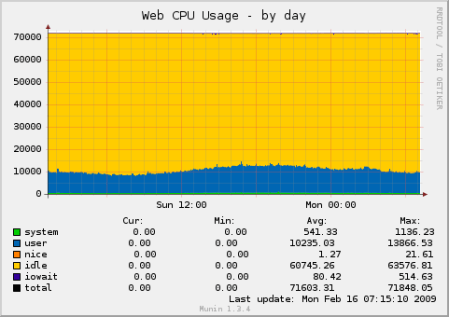
And here is a graph of what the current CPU usage looks like across about 700 CPU cores. As you can see there is plenty of idle CPU for those big spikes or in case one of the other 2 data centers fail and we have to route more traffic to this one.